Two Chinese nationals were recently charged with laundering over $100 million worth of cryptocurrency from the hack of a cryptocurrency exchange. The funds were stolen by North Korean actors in 2018, as detailed in the civil forfeiture complaint also unsealed today.
In the two-count indictment unsealed today in the District of Columbia, 田寅寅 aka Tian Yinyin, and 李家东 aka Li Jiadong were charged with money laundering conspiracy and operating an unlicensed money transmitting business.
“These defendants allegedly laundered over a hundred million dollars worth of stolen cryptocurrency to obscure transactions for the benefit of actors based in North Korea,” said Assistant Attorney General Brian A. Benczkowski of the Justice Department’s Criminal Division. “Today’s actions underscore that the Department will pierce the veil of anonymity provided by cryptocurrencies to hold criminals accountable, no matter where they are located.”
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) also announced they have sanctioned the two Chinese nationals involved who are linked to Lazarus Group, a U.S.-designated North Korean state-sponsored malicious cyber group.
As a result of today’s action, all property and interests in property of these individuals that are in the United States or in the possession or control of U.S. persons must be blocked and reported to OFAC. OFAC’s regulations generally prohibit all dealings by U.S. persons or within the United States (including transactions transiting the United States) that involve any property or interests in property of blocked or designated persons.
In addition, persons that engage in certain transactions with the individuals designated today may themselves be exposed to the designation. Furthermore, any foreign financial institution that knowingly facilitates a significant transaction or provides significant financial services for any of the individuals designated today could be subject to U.S. correspondent account or payable-through sanctions.
“The North Korean regime has continued its widespread campaign of extensive cyber-attacks on financial institutions to steal funds,” said Treasury Secretary Steven T. Mnuchin. “The United States will continue to protect the global financial system by holding accountable those who help North Korea engage in cyber-crime.”
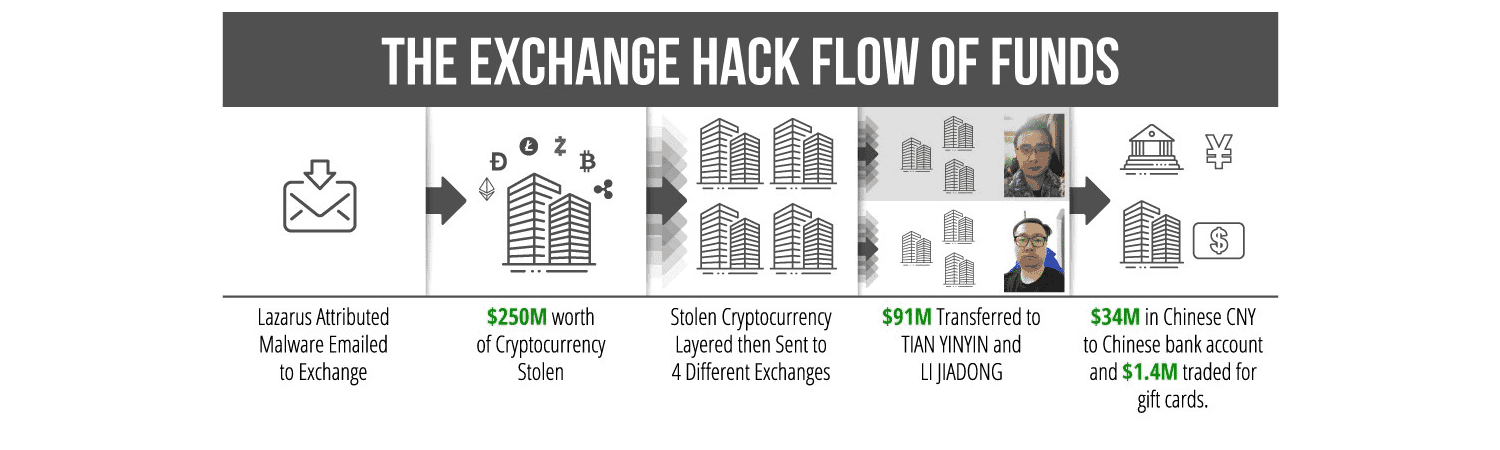
According to the pleadings, in 2018, North Korean co-conspirators hacked into a virtual currency exchange and stole nearly $250 million worth of virtual currency. The funds were then laundered through hundreds of automated cryptocurrency transactions aimed at preventing law enforcement from tracing the funds. The North Korean co-conspirators circumvented multiple virtual currency exchanges’ know-your-customer controls by submitting doctored photographs and falsified identification documentation. A portion of the laundered funds was used to pay for infrastructure used in North Korean hacking campaigns against the financial industry.
The pleadings further allege that between December 2017 and April 2019, Yinyin and Jiadong laundered over $100 million worth of virtual currency, which primarily came from virtual currency exchange hacks. The defendants operated through independent as well as linked accounts and provided virtual currency transmission services for a fee for customers. The defendants conducted business in the United States but at no time registered with the Financial Crimes Enforcement Network (FinCEN).
The pleadings further allege that the North Korean co-conspirators are tied to the theft of approximately $48.5 million worth of virtual currency from a South Korea-based virtual currency exchange in November 2019. As with the prior campaign, the North Korean co-conspirators are alleged to have laundered the stolen funds through hundreds of automated transactions and submitted doctored photographs and falsified identification documentation. The pleadings identify how the North Korean co-conspirators used infrastructure in North Korea as part of this campaign.
The civil forfeiture complaint specifically names 113 virtual currency accounts and addresses that were used by the defendants and unnamed co-conspirators to launder funds. The forfeiture complaint seeks to recover the funds, a portion of which has already been seized.
The charges in the pleadings are merely allegations, and all defendants are presumed innocent until proven guilty beyond a reasonable doubt in a court of law.
“Today, we are publicly exposing a criminal network’s valuable support to North Korea’s cyber heist program and seizing the fruits of its crimes,” said Assistant Attorney General John C. Demers of the Justice Department’s National Security Division. “This case exemplifies the commitment of the United States government to work with foreign partners and the worldwide financial services industry to disrupt this blended threat.”
“The hacking of virtual currency exchanges and related money laundering for the benefit of North Korean actors poses a grave threat to the security and integrity of the global financial system,” said U.S. Attorney Timothy J. Shea of the District of Columbia. “These charges should serve as a reminder that law enforcement, through its partnerships and collaboration, will uncover illegal activity here and abroad, and charge those responsible for unlawful acts and seize illicit funds even when in the form of virtual currency.”
“North Korea continues to attack the growing worldwide ecosystem of virtual currency as a means to bypass the sanctions imposed on it by the United States and the United Nations Security Council. IRS-CI is committed to combatting the means and methods used by foreign and domestic adversaries to finance operations and activities that pose a threat to U.S. national security,” said Internal Revenue Service-Criminal Investigation (IRS-CI) Chief Don Fort. “We will continue to push our agency to the forefront of complex cyber investigations and work collaboratively with our law enforcement partners to ensure these nefarious criminals are stopped and that the integrity of the United States financial system is preserved.”
“The FBI will continue to actively work with our domestic and international law enforcement partners to identify and mitigate the illicit movement of currency,” said Assistant Director Calvin Shivers of the FBI’s Criminal Investigative Division. “Today’s indictment and sanctions send a strong message that the United States will not relent in holding accountable bad actors attempting to evade sanctions and undermine our financial system.”
“This case shows how important robust partnerships across the U.S. Government are in disrupting criminal actors,” said Acting Assistant Director Robert Wells of the FBI’s Counterintelligence Division.
“This indictment shows what can be accomplished when international law enforcement agencies work together to uncover complex cross-border crimes,” said Acting Executive Associate Director Alysa Erichs of U.S. Immigration and Customs Enforcement’s Homeland Security Investigations (HSI). “HSI is committed to upholding the rule of law and investigating those that would steal cryptocurrency for their illicit purposes.”
According to the pleadings, in 2018, North Korean co-conspirators hacked into a virtual currency exchange and stole nearly $250 million worth of virtual currency. The funds were then laundered through hundreds of automated cryptocurrency transactions aimed at preventing law enforcement from tracing the funds. The North Korean co-conspirators circumvented multiple virtual currency exchanges’ know-your-customer controls by submitting doctored photographs and falsified identification documentation. A portion of the laundered funds was used to pay for infrastructure used in North Korean hacking campaigns against the financial industry.
The pleadings further allege that between December 2017 and April 2019, Yinyin and Jiadong laundered over $100 million worth of virtual currency, which primarily came from virtual currency exchange hacks. The defendants operated through independent as well as linked accounts and provided virtual currency transmission services for a fee for customers. The defendants conducted business in the United States but at no time registered with the Financial Crimes Enforcement Network (FinCEN).
The pleadings further allege that the North Korean co-conspirators are tied to the theft of approximately $48.5 million worth of virtual currency from a South Korea-based virtual currency exchange in November 2019. As with the prior campaign, the North Korean co-conspirators are alleged to have laundered the stolen funds through hundreds of automated transactions and submitted doctored photographs and falsified identification documentation. The pleadings identify how the North Korean co-conspirators used infrastructure in North Korea as part of this campaign.
The civil forfeiture complaint specifically names 113 virtual currency accounts and addresses that were used by the defendants and unnamed co-conspirators to launder funds. The forfeiture complaint seeks to recover the funds, a portion of which has already been seized.
The charges in the pleadings are merely allegations, and all defendants are presumed innocent until proven guilty beyond a reasonable doubt in a court of law.
North Korea’s History of Malicious Cyber-Enabled Activities
On September 13, 2019, Treasury identified North Korean hacking groups commonly known within global cybersecurity private industry as “Lazarus Group,” “Bluenoroff,” and “Andariel” as agencies, instrumentalities, or controlled entities of the Government of North Korea, pursuant to E.O. 13722, based on their relationship to the Reconnaissance General Bureau (RGB), North Korea’s primary intelligence agency. Lazarus Group, Bluenoroff, and Andariel are controlled by the U.S.- and United Nations (UN)-designated RGB.
North Korea’s malicious cyber activity is a key revenue generator for the regime, from the theft of fiat currency at conventional financial institutions to cyber intrusions targeting cryptocurrency exchanges. The August 2019 UN Security Council 1718 Committee Panel of Experts report estimates that North Korea had attempted to steal as much as $2 billion, of which $571 million is attributed to cryptocurrency theft. This revenue allows the North Korean regime to continue to invest in its illicit ballistic missile and nuclear programs.
Given the illicit finance risk that cryptocurrency and other digital assets pose, in June 2019 the Financial Action Task Force (FATF) amended its standards to require all countries to regulate and supervise such service providers, including exchangers, and to mitigate against such risks when engaging in cryptocurrency transactions. Virtual asset service providers and traditional institutions should remain vigilant and alert to substantial changes in customers’ activities, as their business may be used to facilitate the transfer of stolen proceeds. The United States is particularly concerned about platforms that provide anonymous payment and storage functionality without transaction monitoring, suspicious activity reporting, or customer due diligence, among other obligations.
DPRK cyber actors actively target the cryptocurrency community and are known to employ a variety of fake cryptocurrency trading programs that contain malware. In April 2018, the Lazarus Group leveraged previously used malware code from the now-defunct cryptocurrency application Celas Trade Pro — software both developed and offered by the Lazarus Group registered website called Celas Limited. Creating illegitimate websites and malicious software to conduct phishing attacks against the virtual currency sector is a pattern previously seen from North Korean cybercriminals.
DPRK malicious cyber proceeds are often transferred to cryptocurrency exchanges and peer-to-peer marketplaces with negligible customer screening compliance programs, or individual peer-to-peer or over-the-counter traders operating on exchanges that do not screen their customers. Stolen cryptocurrency may be layered using various schemes, traded for fiat currency, deposited in bank accounts, and traded for gift cards. Proceeds from DPRK malicious cyber activities often end up at Chinese financial institutions.